Whether your team is grouped together across multiple locations or they’re virtual employees, and whether its been this way for years or you’re new to managing a distributed workforce, it’s important to regularly evaluate what’s working and what’s not.
Although the benefits of having geographically dispersed teams can be numerous, the challenges that coincide with it can be difficult to deal with if a company is ill-equipped to manage the people, technology, brand, and culture across multiple locations.
Let’s break down four struggles involved with leading virtual teams and managing multiple locations, and how you can effectively approach managing dispersed employees to ensure the team stays connected and technology runs smoothly.
1. Managing Cybersecurity and Compliance with a Decentralized Workforce
The biggest technical challenge of having virtual employees and people using mobile devices is protecting sensitive data through cybersecurity measures.
It seems like nearly every day we hear about another cyber-attack or data breach in a large organization. It doesn’t matter how big or small your organization is, though – every company has to take cybersecurity seriously.
A breach can happen anywhere and to anyone, whether they’re working in a corporate office or a home office.
When the company’s or clients’ personal data becomes compromised, there are major costs both to the company’s finances and to its reputation. Luckily, it’s becoming easier and easier to implement measures that prevent cyber hacks.
Keeping information secure online is not just the responsibility of IT anymore – you have to get everyone on board.
Allowing employees to use or bring their own devices (BYOD) can save your company a ton of money on technology expenditures. However, you’ll want to have your IT department create a plan for mobile device management (MDM).
If the strategy and details of your MDM plan are unclear, employees likely won’t take it seriously and will just work around the constraints of IT wherever they can. When they’re accessing sensitive company and/or client data, not having the right securities in place puts all of that data at risk.
Supplying employees – no matter if they’re working in the office or remotely – with up-to-date, secure technology will allow employees to feel more productive knowing they’ll have everything they need to work from anywhere while also having their data protected.
If the importance of complying with cybersecurity measures is lost on your employees, or they’re simply unaware of what they need to do to keep data safe online, consider how your cybersecurity training could be more effective.
Compliance training in general, whether it’s cybersecurity, harassment, safety, HIPAA, etc. tends to just be a checkbox to mark off, without much focus on whether training is being retained and creating behavior changes with employees – which is the goal of training, after all.
As a manager, it’s important to connect with HR and leadership teams to ensure your employees have the resources they need to stay up to date on the latest safety and compliance regulations. If you’re looking for compliance training that actually prevents infractions and protects your company from lawsuits, you need modern solutions that are about more than checking off the “completed” box.
Deliver Training That Will Make a Positive Impact on Your Employees
Microlearning videos are powerful for delivering necessary training because they’re more engaging for learners and get key concepts across more efficiently than longer, traditional training.
Rather than taking people off the job for an hour or more at a time for classroom training, microlearning fits within busy schedules and can be taken online on any device, allowing training to happen when and where it’s needed.
If your organization has to deal with fitting training in between the flow of customers, like banks or credit unions, you’ll find microlearning videos to be a practical solution to that challenge.
Consumers Credit Union used short, video-based training so their employees wouldn’t have to be taken off the job for long periods of time. They were able to train in between providing service to members, and reduced onboarding costs by $2,000 per employee!
2. Communicating Effectively with Virtual Employees
One of the disadvantages of having people working remotely is the sense of isolation it can bring if the team’s collaboration isn’t strong.
Leading virtual teams requires understanding how to effectively communicate in multiple ways, depending on the task or situation.
When you’ve found talented people who can work remotely and manage their own workloads, collaboration is helpful, but commenting on their every move is detrimental.
Rather than having people doing their own thing in their own corner, you can better connect your virtual employees with the right tools and well-equipped managers.
There are a lot of tools out there for helping your team collaborate, but as a manager, you need to consistently evaluate whether those tools are being used effectively, or if they’re just getting in the way.
It’s also important that employees receive an in-depth overview on the best ways to use each tool so that teams can better collaborate and stay connected. Chat platforms are well suited for some communications, while email or Zoom are better for others:
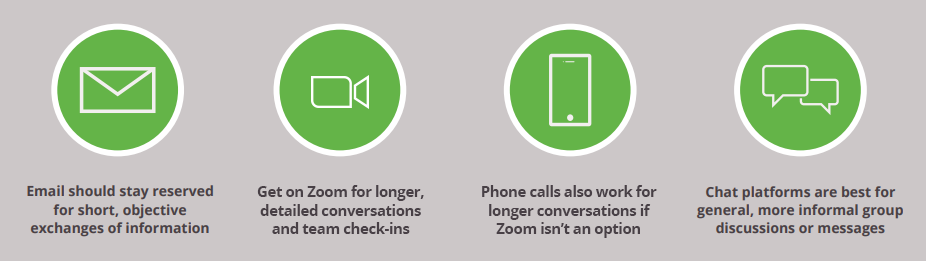
A lot of headaches and mistakes can be circumvented by training managers and employees on the best ways to communicate across their geographically dispersed team. They need to know they can count on each other, and building that trust requires everyone to do their best to communicate fully and clearly.
A hindrance to any team, remote or not, is having a manager who micro-manages employees’ tasks.
Allowing people to be more autonomous in their work will help your company attract and keep talented individuals.
To train your managers on effectively communicating expectations and checking in without micro-managing, look into providing short, engaging, on-demand videos that they can use for quick reference wherever they are.
The topic of communication is massive, and the soft skills involved can be constantly improved upon.
Breaking it down into smaller subjects in microlearning videos, whether they’re covering concrete hard skills or more abstract soft skills, makes the information easier to apply on the job.
3. Maintaining Focused Branding and a Connected Culture
Another way that Consumers Credit Union has kept their distributed workforce connected is by creating custom training content that reinforces their brand and culture across locations. Branding is crucial for any company to see sales growth and move up market, so keeping the company’s mission and message cohesive should be a priority for any company.
It can be difficult enough to maintain a brand and a strong culture when everyone is in the same building but adding geographical distance between teams makes that even more of a challenge.
Your brand and your culture go hand in hand. They reflect and strengthen each other. They create unity internally and externally.
If your brand message and style isn’t consistently delivered by every employee, it weakens the credibility of your company in the eyes of consumers.
This is why having a central hub, like an LMS, for branded content and consistent training on the products and services you offer is key.
If culture isn’t properly managed, negative feelings can be harbored between on-site and remote employees or corporate versus remote sites – one group can feel as though the other group is being treated as “special” while they feel ignored. It’s always smart to regularly conduct anonymous surveys to get a read on the culture and find out where there may be issues.
Having a strong brand, a great culture, and plenty of professional growth opportunities are what attract talented people to your organization.
When your location is decentralized, that opens up a lot of doors for hiring the best of the best, but you don’t want your company culture and management to give them a reason to take their talent elsewhere once they get an inside look.
The challenges of keeping a distributed workforce connected through healthy communication and a solid culture are highly dependent on those in leadership positions.
4. Recognizing Talent Across Hybrid Settings
According to SHRM, proximity bias is the tendency for people in authority to show favoritism or preferential treatment to employees who are closest to them physically.
As the number of employees and organizations moving toward progressive hybrid work models increases, it’s critical that managers place trust in their employees to meet their duties and responsibilities, no matter where they may be located.
This means creating safe spaces for open communication with your employees and recognizing the different forms talent may look like. Instead of measuring success based on whether an employee is in the office five days a week, look for employees who take initiative and aren’t afraid to bring their ideas into the conversation.
In order to engage and retain your organization’s employees, managers need to recognize their employees for their exceptional work so that they continue to feel seen and empowered to take the next steps to excel in their careers.
Check out our Expert Insight Series: Thrive While Working Remotely with Mike Gutman to learn how you can further set your employees up for success:
Some leaders are great with managing teams in person, but they struggle with motivating and overseeing their teams from a distance. Addressing these four challenges early on and putting them at the forefront of your organization’s leadership strategy will help create an agile workforce and company with high employee engagement, internal promotions, and employee retention.


